An attack surface is the totality of potential entry points that can be used to access an IT environment, typically for the purpose of launching a cyberattack.
IT Jargon Explained
What is an Attack Surface?
“Attack surface” is a concept that's gained increased interest recently. Google Trends shows steady growth in “attack surface” as a search term over the past five years.
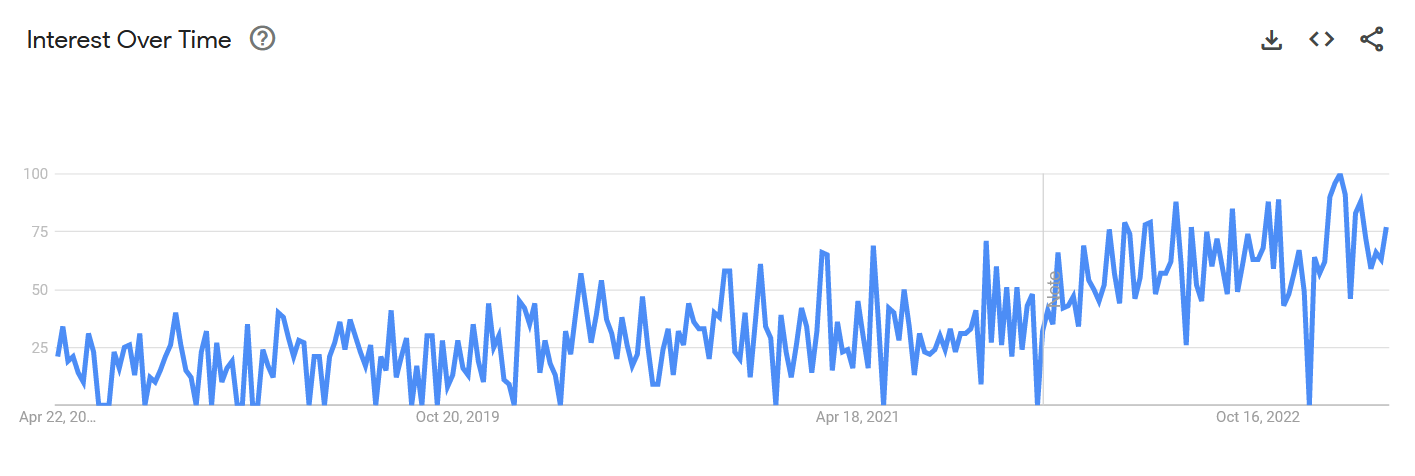
Google Trends results for 'attack surface' from April 2018 to April 2023
The growth in interest in attack surfaces as a topic logically coincides with the growth of actual attack surfaces. Two-thirds of organizations claim their attack surfaces grew in the past year. Expansion of Everywhere Work and increased usage of internet-accessible assets, such as cloud applications and IoT endpoints, are among the main drivers.
The situation has reached a point where it's critical for IT and security professionals to not only be knowledgeable about the topic, but also be able to take action to identify, manage and reduce their organization’s attack surfaces.
What is an attack surface in cybersecurity?
As with any technical concept, when discussing attack surfaces, it’s important to understand the terminology associated with the concept so that all parties are speaking a common language. Thus, that’s where we’ll begin our coverage of attack surfaces.
Definitions of “attack surface” are varied. Here are some from leading authorities in the cybersecurity space:
- Australian Cyber Security Center (ACSC): “The amount of ICT (information and communications technology) equipment and software used in a system.”
- National Institute of Standards and Technology (NIST): “The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment.”
- Open Worldwide Application Security Project (OWASP) Foundation: “The Attack Surface describes all of the different points where an attacker could get into a system, and where they could get data out.”
We'll define “attack surface” as the totality of potential entry points that can be used to access an IT environment, typically for the purpose of launching a cyberattack. Those entry points can be digital, physical or human.
What is a digital attack surface?
Digital attack surfaces are comprised of anything and everything that expose an organization’s IT infrastructure and systems — whether in the cloud or on-premises — to outside parties with internet connections. In other words, the digital entry points to your environment.
Some consider digital attack surfaces to basically be network attack surfaces as they consist of all the hardware and software connected to a company’s network. However, the components that make up a digital attack surface are multiple and varied. Beyond simply “hardware” and “software,” those components include, but aren't limited to:
- Code.
- Internet-facing applications and servers.
- Misconfiguration of IT systems, assets and tools.
- Obsolete IT assets, like devices and applications.
- Passwords.
- Ports.
- Rogue access points.
- Shadow IT.
- Shared database.
- Shared directories.
- Vulnerabilities in software, firmware and operating systems.
- Websites.
Attackers can exploit all of these to gain access to an IT environment.
What is a physical attack surface?
Physical attack surfaces refer to any physical object which could be targeted by malicious actors. Much like some consider digital attack surfaces to be network attack surfaces, it'd almost be fair to classify physical attack surfaces as endpoint attack surfaces as they are commonly comprised primarily of desktop computers, laptops, mobile devices and IoT devices. These devices often find their way into the hands of bad actors after being lost or stolen.
In addition to endpoints, physical attack surfaces also consist of:
- USB ports.
- Security cameras and USB webcams.
- Hard drives.
- Networking hardware.
- Office equipment like printers.
- Entry points to physical locations such as offices and data centers.
- User data and login credentials stored on discarded hardware or written on paper.
- Lost employee ID cards, key fobs or authentication tokens.
Basically, if it’s something you can physically touch, it’s part of a physical attack surface.
What is a human attack surface?
Much attention is given to the attack surfaces of networks and endpoints, but there’s another attack surface that's often overlooked: the human attack surface. That may explain why 74% of the breaches analyzed for the 2023 Data Breaches Investigation Report (DBIR) from Verizon involved a human element.
Human attack surfaces are formed through the failure of users or administrators to adhere to security best practices. These failures mainly consist of people falling for social engineering attacks. According to the Verizon report, phishing and pretexting – which is often used in conjunction with phishing – are the two types of social engineering that claim the most victims. No wonder 43% of organizations surveyed for the Press Reset: A 2023 Cybersecurity Status Report have experienced a phishing attack in the past two years.
Other components that make up a human attack surface may include:
- Failure to patch systems regularly.
- Use of weak and repeated passwords.
- Improper assignment of user privileges.
- Propping the door to an office building open.
- Letting unauthorized persons tailgate or piggyback into a secure space.
- Failure to eliminate network design flaws.
- Allowing sensitive information to be stolen via shoulder surfing.
- Falling for a baiting attack by plugging an unknown USB drive into a computer.
- Improperly discarding of sensitive data.
The list is endless. And while the examples shared thus far are typically unintentional acts that can be attributed to naiveté and negligence, human attack surfaces also include the intentional actions of malicious insiders. According to the Cybersecurity & Infrastructure Security Agency (CISA), an intentional threat is “the potential for an insider to use their authorized access or understanding of an organization to harm that organization.”
Note that different attack vectors can be considered part of multiple types of attack surfaces. For instance, the propped door example could be considered part of both a human attack surface since it was propped open by a human and a physical attack surface as the door is a physical object offering entry to a physical location. What’s ultimately important isn't the type of attack surface an attack vector is attributed to, but that you identify, manage and — where possible — eliminate the vector.